A Crypto system is an implementation of cryptographic techniques and their accompanying infrastructure to provide information security services. A cryptosystem is also referred to as a cipher system.
A simple model of a cryptosystem that provides confidentiality to the information being transmitted. This basic model is depicted in the illustration below.
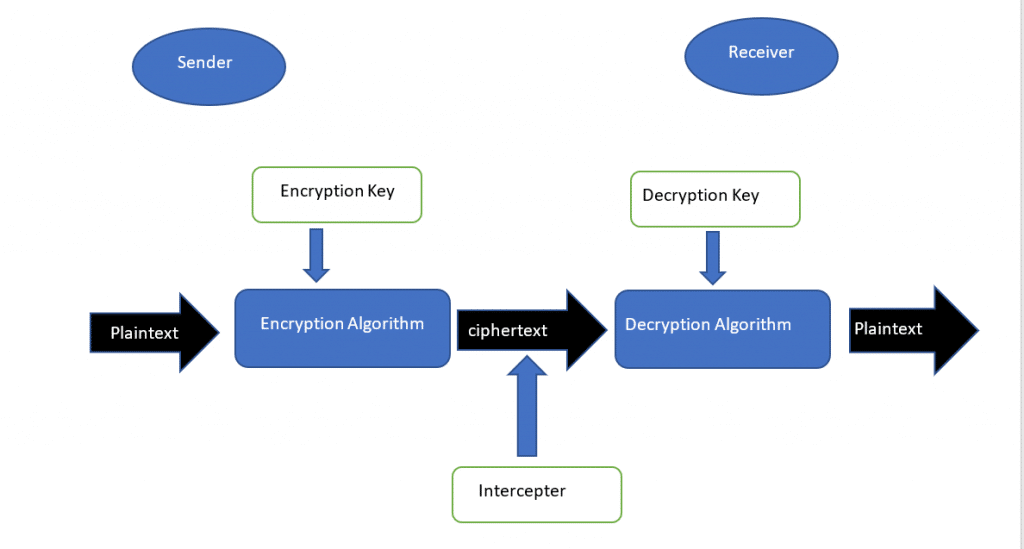
The illustration shows a sender who wants to transfer some sensitive data to a receiver in such a way that any party intercepting or eavesdropping on the communication channel cannot extract the data.
The objective of this simple cryptosystem is that at the end of the process, only the sender and the receiver will know the plaintext.
Components of a Cryptosystem:
• Plaintext: It is the input message that needs to be encrypted.
• Encryption key: The sender of the plaintext requires this key for encryption.
• Encryption algorithm: This cryptographic algorithm takes the plaintext and the encryption key as input to output the encrypted message.
• Ciphertext: It is the encrypted message output.
• Decryption key: The receiver requires this key for decryption.
• Decryption algorithm: This is a cryptographic algorithm that reverses the encryption. It takes the ciphertext and decryption key as input and outputs the plaintext.
Types of cryptosystems
Based on the differences in encryption and decryption, we can categorize the cryptosystems into the following two types:
• Symmetric Cryptosystem
• Asymmetric Cryptosystem
The fundamental difference between them is that the symmetric cryptosystem only involves one key that the system uses for encryption and decryption. The asymmetric cryptosystem uses two keys (private and public) for encryption and decryption.
- Symmetric cryptosystem
Since the symmetric cryptosystem uses the same key for encryption and decryption, the sender and receiver need to know the key before exchanging messages. For this, the system employs key exchange protocols (like the Diffie-Hellman Protocol) to ensure that the sender and receiver agree on the secret key before starting the communication. The illustration below depicts symmetric encryption and decryption using the same key:
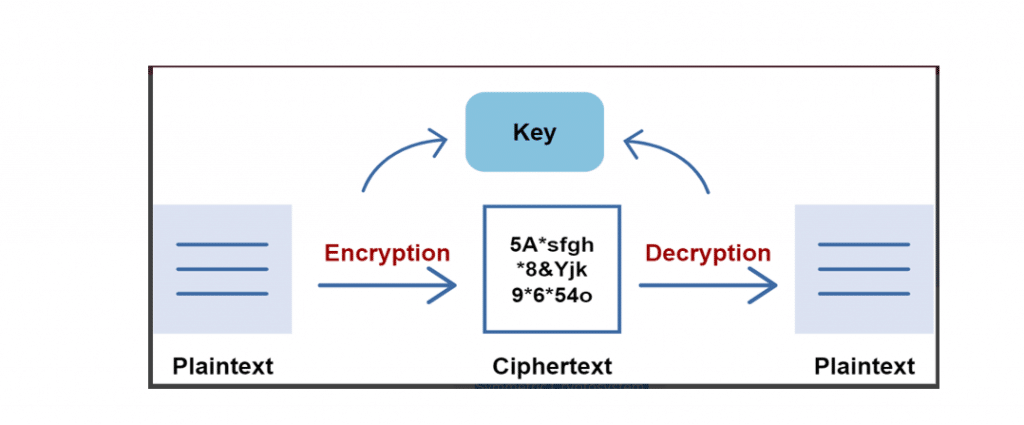
For the encryption algorithms, the symmetric cryptosystem uses AES-128, AES-192, and AES-256. The encryption process is generally faster in symmetric cryptosystems due to the smaller key lengths. The drawback of this system is that the senders and receivers need to exchange keys before decrypting the message. If the keys are not changed regularly, the system will be prone to attacks since an attacker can use the leaked key to disrupt the communication. The symmetric cryptosystem uses MACs to provide integrity and authentication.
- Asymmetric cryptosystem
The asymmetric cryptosystem overcomes the symmetric cryptosystem challenges by eliminating the need to pre-sharing the key before communication. The asymmetric cryptosystem used two keys (private and public) that are mathematically related to each other. The strength of security lies in these keys’ properties since it is computationally infeasible to calculate one key using the other. Each sender and receiver will have their private-public key pair in this system. Suppose A wants to send a message to B, A will need to use B’s public key to encrypt the message, and B will decrypt the message using their private key.
The illustration below depicts asymmetric encryption and decryption using two keys: Asymmetric Crypto System.
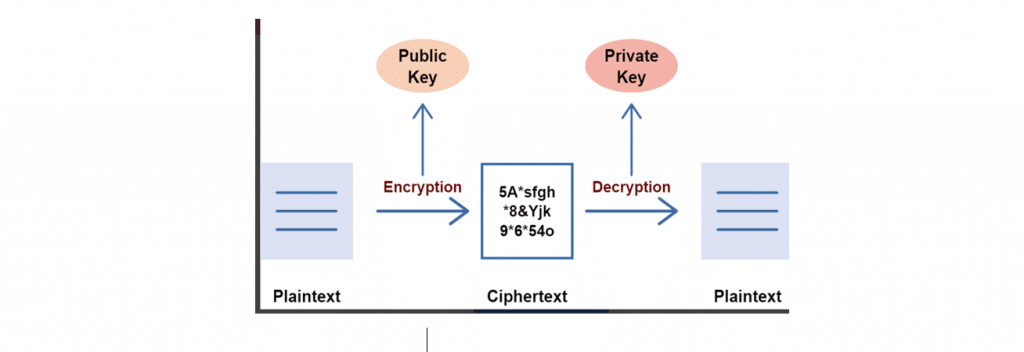
For the encryption algorithms, the asymmetric cryptosystem uses El Gamal Encryption or RSA Encryption schemes. The encryption process is slower than symmetric encryption due to larger key sizes. The asymmetric cryptosystem is more secure since the private and public key pairs are less likely to get leaked and predicted. The asymmetric cryptosystem uses RSA signatures to provide integrity and authentication.
Advantages and Disadvantages of Asymmetric
ADVANTAGES
i. In asymmetric or public key, cryptography there is no need for exchanging keys, thus eliminating the key distribution problem.
ii. The primary advantage of public-key cryptography is increased security: the private keys do not ever need to be transmitted or revealed to anyone.
iii. Can provide digital signatures that can be repudiated
DISADVANTAGES
A disadvantage of using public-key cryptography for encryption is speed: there are popular secret-key encryption methods which are significantly faster than any currently available public-key encryption method.
________________________________________________________________________________



